Summary:
This paper report seems extra into the development in direction of the Info safety programs. This report reveals the significance and the adjustments that a corporation may accomplish by strengthening the IT safety system. We contend that there are a useful job the chief’s approaches that affect the safety system related to many of the situation in a corporation. In some scenario, although replicating upon field-responsibility, the share of those expertise safety strategies carry out to only not work on the planet exemplified by way of enterprise assist and disaster assist ventures. This brings up some intriguing points, although a corporation has demonstrated its accomplishment in growth technique. There are points associated to the best way wherein the framework has been Chosen in addition to actualized which have prompted safety points.
There are consultant adoption diminishes the effectiveness of IT safety investments within the probability of a breach. Opposite to the employment of a variety of IT safety isn’t immediately liable for lowering breaches, nevertheless as a substitute, institutional elements produce the situations beneath that IT safety investments could be simpler. Implications of these findings space unit essential for coverage and observe, the foremost essential of which could be the invention that corporations should consider nevertheless adoption is influenced by institutional elements and the way this may very well be balanced with technological options (Angst, C. M., Block, E. S., D’Arcy, J., & Kelley, Ok., 2017). Specifically, this report outcomes assist the notion that deeper integration of safety into IT-related processes and routines leads to fewer breaches, with the caveat that it takes time for these benefits to be accomplished.
Introduction
Know-how and its crucial elements that performs a serious function in each group. IT safety is a set of safety methods that assist a corporation in stopping any sorts of unauthorized attackers on its asset and IT sector. IT safety helps in blocking the entry of subtle hackers my blocking their asses to this delicate info. Relying upon the aim and the form of info, exercise, there are totally different sorts of a safety technique that may be carried out and even developed as per the requirement. With the variety of particulars and elements that you just simply acquired to put alongside, it’ll be greatest for utilizing strategic designing itemizing examples that be sure that express safety points, motion plans, methods, related knowledge, and issues are going to be enclosed inside the doc.
Extra essential, a corporation platform for IT safety allow cyber-security to develop the infrastructure for personals engaged on the merchandise for info safety, creating throughout the division and useful areas to make sure a robust however versatile safety barrier. The result’s quicker planning and stronger enforcement of safety insurance policies. This creates a capability to realize sustained compliance with group and authorities requirements on the safety, a complete, well-documented process and insurance policies. And total cost-effective and saves the corporate revenue by lowering undesirable bills by lowering safety assaults and its aftereffects.
This report will assessment a number of the fundamental points that relate to info safety course of, industrial threats and a few the methods to stop them. Together with the challenges in implementing safety necessities which are concerned in info safety and compliances processes.
Significance of data safety:
Each group is constructed with a stable base of sources, it may be info they deal with or it may be the individuals who work for the expansion of the group. In actual fact, respective of the useful resource you will need to defend them. the way forward for a corporation is dependent upon its belongings. And defending then ought to be the precedence of a corporation. Regardless that IT safety and knowledge safety is often thought-about comparable, they’re two various kinds of safety. The kind of safety that focuses to safe delicate info and develop software defend delicate organizational info is referred to be info safety, whereas IT safety focuses extra on securing digital knowledge and community safety from hackers and different malicious assaults.
Widespread threats to IT safety
IT safety faces threats of various types. A standard risk that’s well-liked within the business is malware, or malicious software program, which can come in several variations to contaminate community gadgets, together with:
• Ransomware
• Adware
• Viruses
It is very important have dependable safety and greatest observe consciousness to remain protected. Studying extra and making an attempt to undertint any malicious exercise is step one to be ready on these assaults.
Supply: COMODO creating belief on-line
How IT safety is helpful?
IT safety prevents malicious threats and potential safety breaches which will have a big affect in your group. While you enter your inside firm community, IT safety helps guarantee solely licensed customers can entry and make adjustments to delicate info that resides there. IT safety works to verify the confidentiality of your group’s info.
Few sorts of IT safety
• Community safety
Community safety is employed to foresee unauthorized or malicious customers from acquiring inside your community. This ensures that usability, reliability, and integrity are uncompromised. Such a safety is essential to stop a hacker from accessing info inside the community. It conjointly prevents them from negatively poignant your customers’ potential to entry or use the community. Community safety has grow to be increasingly more troublesome as companies improve the variety of endpoints and migrate companies to the general public cloud.
• Web safety
Web safety includes the safety of data that’s despatched and obtained in browsers, moreover as community safety involving web-based functions. These protections are designed to look at incoming community visitors for malware moreover as undesirable visitors. This safety may can be found within the form of firewalls, antimalware, and antispyware.
• Endpoint safety
Endpoint safety gives safety on the machine stage. Units that might be secured by endpoint safety embody cell telephones, tablets, laptops, and desktop computer systems. Endpoint safety can forestall your gadgets from accessing malicious networks that might be a risk to your group. Superior malware safety and machine administration package deal are samples of endpoint safety.
• Cloud safety
Because the expertise advances Functions, knowledge, and knowledge space are shifting to the cloud, which suggests customers space unit connecting on to the online and don’t appear to be protected by the conventional safety stack. Cloud safety will facilitate safe the utilization of software-as-a-service (SaaS) functions and subsequently the general public cloud. and cloud-based unified risk administration (UTM) will assist in points primarily based on cloud safety.
Significance of Safety Strategic Plan for a Enterprise
A well-designed advertising and marketing technique the easiest way to take a product to a buyer, equally the planning a greater technique and motion plans to safe enterprise safety is extra essential for its enterprise. Safety strategic plans could be developed by taking a number of factors in thoughts together with enterprise info knowledge, digital belongings, and knowledge, the situation of the group, inside private safety, and company relationships. Under are a number of the explanation why it can be crucial for any group to have a robust safety strategic plan.
1. A safety strategic plan defines the situation of the safety wherein enterprise must run. This gives a objective and goal that must be ensured any group to take care of or enhance its safety stage.
2. A safety strategic plan helps in managing safety dangers. With the assistance of this plan, a well-documented safety measure is developed. This may put together a enterprise to investigate the affect and outcomes of any threats and dangers on an assault. This is among the greatest methods in terms of enterprise operations even when there are doable safety points which are essential to be addressed in the intervening time or sooner or later.
three. A safety strategic plan will assist in gathering all of the entities which are current within the enterprise and practices collectively to develop an understanding concerning their obligations in terms of preserving the security and safety of the company location. This doc may assist outline specific phrases and directions which may make the plan extra understandable.
four. A safety strategic plan will assist in making ready an motion plan and choosing methods that may promote the procedures for creating the safety both in a selected enterprise space or your entire office. This will help the group to outline its safety restrictions and set up procedures the place it wish to take the safety insurance policies and protocols of the business.
Supply: IT SECURITY & STRATEGY
Human think about IT safety:
The human issue is a standard think about IT safety, typically individuals could take cybersecurity requirements too casually, resulting in theatrical significances for the organizations they work for.
Just lately WannaCry ransomware epidemic, there’s a main function performed by the human think about making group worldwide helpless. Two months after the unveiled weaknesses had been patched with a brand new replace from Microsoft, many companies world wide nonetheless hadn’t up to date their programs. Quite a few circumstances non-IT staff are thought-about because the weakest hyperlink, that is due to these workforces with native administrator rights who disabled safety options on their computer systems and unknowingly will unfold the an infection from their laptop onto your entire firm community.
Inside danger:
In contradiction of the setting of a fancy and rising cyber risk background, the place 57% of industries now assume their IT safety will turn into compromised, companies are additionally awakening as much as the truth that one of many main chinks of their armor towards web threats is their very own workforces. In actual fact, 52% of companies admit that personnel is their largest softness in IT safety, with their insensitive actions pushing enterprise IT safety technique at risk.
The fear of being put in danger from inside could be seen clearly in the truth that for industries, the highest three cybersecurity fears are all associated to human elements and member of staffs actions. The desk beneath reveals that industries are attentive of how simple it’s for worker/human error to affect their company’s safekeeping. They concern most about staff sharing delicate knowledge through cellular gadgets (47%), the lack of cellular gadgets exposing their firm to danger (46%) and using inappropriate IT belongings by way of personnel (44%).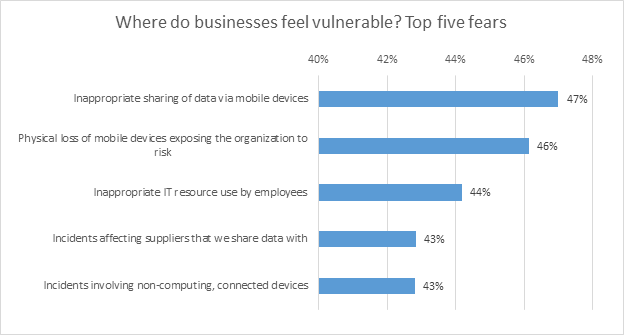
supply: IT Safety Dangers Survey 2017, international knowledge
Greatest Practices in IT safety:
It the final word objective of a corporation to safer. Many of the safety workforce agrees that not a matter what they do to safe the safety there may be at all times one thing inflicting a breach within the system.
Regardless that safety crews have been combating a scenario of continually altering exterior assaults for years, now they’re additionally chargeable for addressing the danger of insider breaches. The truth is, nearly all of administrations will face some type of breach, whether or not it comes from exterior or insider threats.
To be sure you’re outfitted, you will need to take a step-by-step strategy along with your institution’s safety. Under are a number of cybersecurity greatest practices that may be thought-about for growing the IT safety
Itemizing a number of Cybersecurity Greatest Practices
It is very important take step-by-step strategy inside a corporation’s safety. These cybersecurity greatest practices could also be thought-about
1. Observe correct IS Governance Technique
Creating and preserving an info safety define is a good place to start out. This define is extra essential than each shiny software in your safety stack, because it ought to align your assure methods and backing the business.
When selecting considered one of these approaches, affirm your program gives the aptitude to interact a risk-based methodology and allows your teams to sense occasions, examine efficiently, and react rapidly.
2. Finish Information Loss
Most companies depend on a member of employees belief, however that received’t cease shedding knowledge from the corporate. A latest examine of greater than 1,500 safety professionals uncovered that knowledge exfiltration from an endpoint is the highest safety fear of 43% of them. Now, greater than ever, it’s enormously crucial to manage entry, overseer distributors and companies in addition to staff, and know what your shoppers are doing with enterprise knowledge to scale back knowledge leakage.
three. Establish Insider Danger
It’s actually that staff are your main belongings, however additionally it is true that they will also be the most important danger. Though well-trained staff could be your safety entrance line, you continue to need expertise as your final line of safety. Observing consumer exercise means that you can detect illegal efficiency and confirm consumer actions should not violating safety coverage. Insider threats could go unnoticed, however the truth of the matter is insider breaches are awfully costly.
four. Backing Up info
Backing up recordsdata could seem like frequent sense, however any enterprise that has been affected with ransomware like Petya or Wannacry is an ideal instance for telling how essential it’s to safeguard this greatest observe. It’s essential for the company to have a full working again up of the entire knowledge not just for a routine safety objective but in addition for any potential rising assaults.
5. Mitigate Social Engineering
The expertise and IT safety insurance policies implementation doesn’t substitute the necessity for frequent sense or take away human error. Social engineering methods have been used successfully for many years by buying login info and call with encrypted recordsdata. Efforts could come from emails, messages or different technique of communications. The most effective protection is to create consciousness for the working group.
6. Educate and create consciousness to customers
Regardless of how good the individuals are, nonetheless they’re the weakest hyperlink in terms of info safety. However this don’t imply the threats can’t be prevented by the danger by way of continuously educating the customers on cybersecurity greatest practices. All of the coaching applications ought to embrace the best way to determine a phishing e mail, generate and maintain robust passwords, keep away from unsafe functions, guarantee treasured info shouldn’t be taken out of the institution.
In these applications may really feel like unvalued waste of labor hours however in future it can crate an affect to the customers to observe the practices they be taught. Discovering resourceful methods to make the coaching extra entertaining will assist extra in making this system profitable.
7. Plan utilization insurance policies for New Personnel and third Events
To bolster and simplify the training for cybersecurity greatest practices you give your customers, it’s best to clearly framework the requirements and expectations your organization has with regard to IT safety whenever you first rent them. It is suggested to verify employment contracts clearly describe these safety necessities.
eight. Create an Incident Response Playbook
Regardless of even when one of the best practices is properly adopted, there at all times a change it may fail. In actual fact, almost many of the organizations suffers a safety incident a minimum of as soon as an yr. In case of such incident having a response, plan laid ready a head of time will assist to shut any vulnerabilities and assist in limiting the injury of a breach.
9. Replace Software program and Methods
The best and typically the best solution to defend towards any assault is my ensuring the all of the software program and utility is UpToDate. Enabling auto replace function will assist the software program to replace itself to the newest stage, this may enhance the safety of the software program to combat towards any potential connect within the business.
10. Uphold Compliance
Optimistically these greatest practices are a helpful coverage for holding a enterprise secure, however you do have one other set of tips accessible to you. Pointers like HIPAA, PCI DSS and ISO gives benchmarks for a way a enterprise ought to handle its safety. Greater than a stress, which you could put together audit logs for, tips will help guiding a enterprise to a safer future.
Conclusion:
A 100% safety shouldn’t be assured by any methodology however securing the info of a corporation a vital a part of its future. IT is a broad space and overlaying your entire sector is like unattainable. But when we observe essential actions, a safe system could be developed which may assist a corporation. Following one of the best practices together with correct safety tips will strengthen the safety of a corporation. Investing in creating IT safety is actually and greatest choice of the enterprise.
References:
- Angst, C. M., Block, E. S., D’Arcy, J., & Kelley, Ok. (2017). When Do It Safety Investments Matter? Accounting for the Affect of Institutional Elements within the Context of Healthcare Information Breaches. MIS Quarterly, 41(three), 893-A8. Retrieved from http://0-search.ebscohost.com.library.acaweb.org/login.aspx?direct=true&AuthType=ip,cpid,url&custid=s4338230&db=buh&AN=124643940
- Arain MA, Tarraf R, & Ahmad A. (2019). Assessing employees consciousness and effectiveness of academic coaching on IT safety and privateness in a big healthcare group. Journal of Multidisciplinary Healthcare, Vol Quantity 12, Pp 73-81 (2019), 73. Retrieved from http://0-search.ebscohost.com.library.acaweb.org/login.aspx?direct=true&AuthType=ip,cpid,url&custid=s4338230&db=edsdoj&AN=edsdoj.0ed455a448494cd384893341db1c3692
- Zdzislaw POLKOWSKI, & Jakub DYSARZ. (2017). It Safety Administration in Small and Medium Enterprises. Buletin Ştiinţific: Universitatea Din Piteşti. Seria Ştiinţe Economice, Vol 16, Iss three, Pp 134-148 (2017), (three), 134. Retrieved from http://0-search.ebscohost.com.library.acaweb.org/login.aspx?direct=true&AuthType=ip,cpid,url&custid=s4338230&db=edsdoj&AN=edsdoj.ff37d3ac7b9d41069911f52ffb93ed00
- Yunsick Sung. (2016). Clever Safety IT System for Detecting Intruders Based mostly on Obtained Sign Power Indicators. Entropy, 18(10), 366. https://doi.org/10.3390/e18100366
- Tenant, R. M. (2017). Easy methods to enhance IT safety. Medical Economics, (17), 13. Retrieved from http://0-search.ebscohost.com.library.acaweb.org/login.aspx?direct=true&AuthType=ip,cpid,url&custid=s4338230&db=edsghw&AN=edsgcl.507862227
- Vinaja, R. (2013). IT safety danger administration: Perceived IT safety dangers within the context of cloud computing. Journal of World Info Know-how Administration, 16(three), 82-84. Retrieved from https://0-search-proquest-com.library.acaweb.org/docview/1435642511?accountid=9864
- Tracy, R. P. (2007). IT safety administration and enterprise course of automation: Challenges, approaches, and rewards. Info Methods Safety, 16(2), 114-122. Retrieved from https://0-search-proquest-com.library.acaweb.org/docview/229552937?accountid=9864
- Web journals
- https://learnabunchofstuff.wordpress.com/2014/11/25/it-security-strategy/
